Challenge Description :
An accountant at your organization received an email regarding an
invoice with a download link. Suspicious network traffic was observed
shortly after opening the email. As a SOC analyst, investigate the
network trace and analyze exfiltration attempts.
Challenge file : HawkEye
Used Tools :
- Wireshark
We got a pcap(Packet Capture) file and our job is to analyze the packets to identify the suspicious traffic by answering 26 questions.
There are many ways to identify the length of the packets.
[+] From the main window of the wireshark at the bottom
or from menus bar “Statistics → Packet Lengths”
[+] Anwser : 4003 [+]
from menus bar “Statistics → Capture file properties”
But we need to convert it to UTC timestamp , I used python script to do this little task .
[+] Anwser : 2019-04-10 20:37:07 UTC [+]
from menus bar “Statistics → Capture file properties”
[+] Anwser : 01:03:41 [+]
link level means at the data link layer in the OSI model which is MAC address of the computer .
from menus bar “Statistics → Endpoints → Ethernet Tab”
first Mac address has 4003 number of packets
[+] Answer : 00:08:02:1c:47:ae [+]
To identify the manufacturer of the NIC(Network interface card) , You have to know what is Mac address
The first 6 hex digits refers to manufacturer , we can identify it using any lookup utility .
[+] Answer : Hewlett-Packard [+]
Using a simple search for Hewlett Packard Headquarter
[+] Answer : Palo Alto [+]
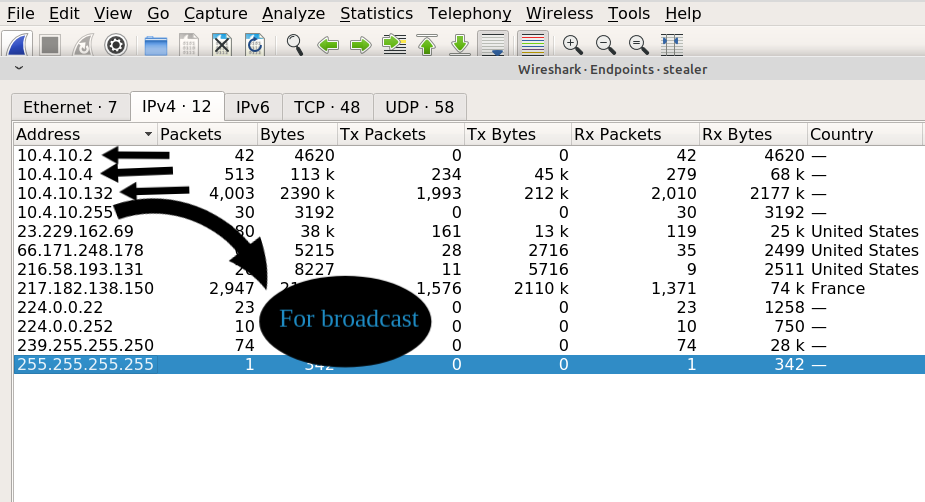
"netmask /24" means there are just 254 endpoints on the network and the last 255 number for broadcast , here we got just 3 endpoints.
from menus bar “Statistics → Endpoints → IPv4 Tab”
[+] Answer : 3 [+]
As we knew the most active computer was "00:08:02:1c:47:ae" has IP address "10.4.10.132" , to get name of this IP we have to find DHCP protocol packets because it have the information about the devices on the network , and that's happen because when a computer connect to the network he request an IP address from DHCP server , That request sent with all information about the client like hostname.
To filter wireshark with dhcp protocol , type bootp
We will find just to "dhcp" packets request and reply
With discovering first packet , checkout host name option
[+] Answer : BEIJING-5CD1-PC [+]
When we using dns filter in wireshark , We will see the response packets came from "10.4.10.4" so it is the server.
[+] Answer : 10.4.10.4 [+]
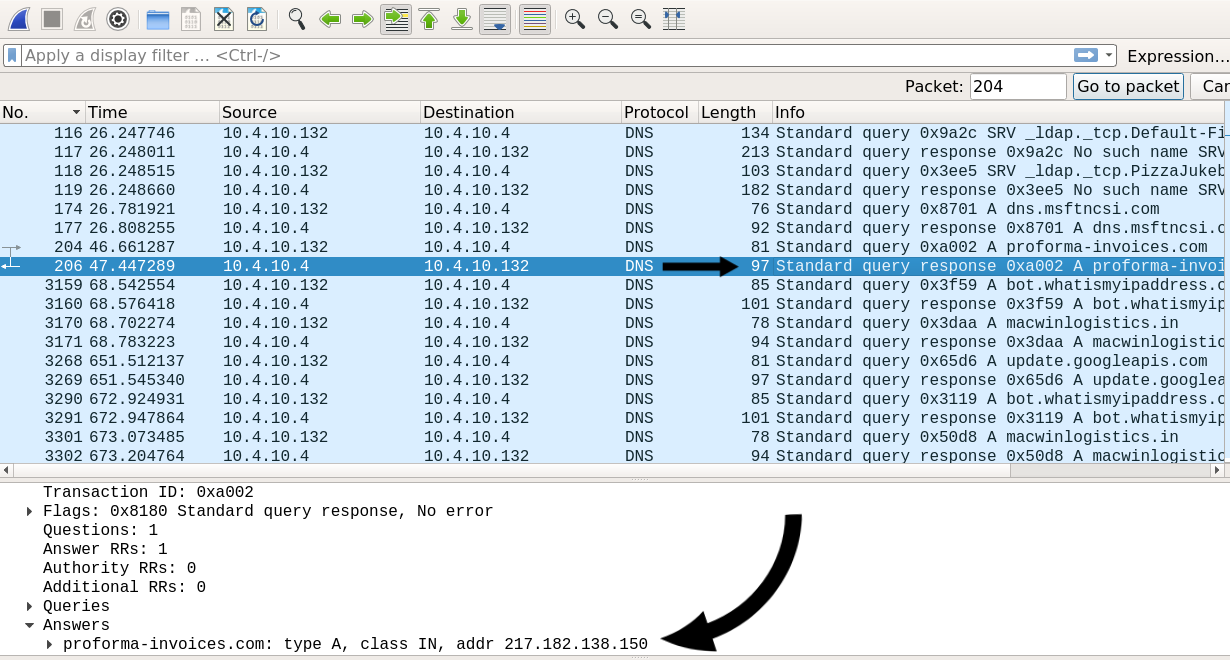
To go to specific packet in wireshark , we can do :
from menus bar “Go → Go To Packet” then write packet number , It will show us the packet and it seems be a DNS query packet , so it has the domain name.
[+] Answer : proforma-invoices.com [+]
As we know the function of DNS server is to convert the domain name to IP address , So if we looked at the response of our previous question , we will get the answer.
[+] Answer : 217.182.138.150 [+]
We can use whois lookup or any IPgeo website to identify the IP location.
[+] Answer : France [+]
We can identify this with the user agent of the host , Because when any host doing http request , he sends a little information about the device like browser name and version and operating system name and version .
[+] Answer : Windows NT 6.1 [+]
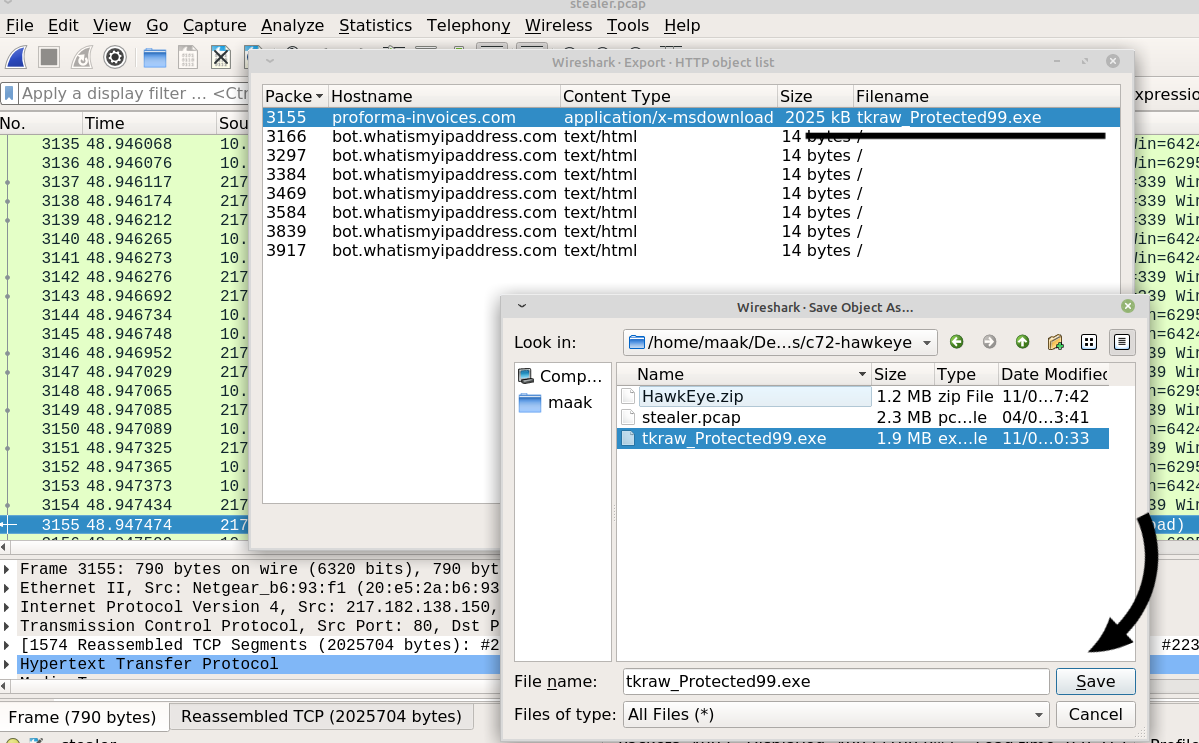
The malicious file was downloaded via HTTP request from proforma-invoices.com website
[+] Answer : tkraw_Protected99.exe [+]
We can calc it using "md5sum" command in linux , or any website the offer md5 hash calc.
But we have to download the file first to calc the hash.
from menus bar “File → Export Objects → HTTP” then select the file we need to download then save it.
After downloading the file we will calc the hash using md5sum command in linux.
[+] Answer : 71826ba081e303866ce2a2534491a2f7 [+]
Upload the file to virustotal.com and look for Malwarebytes , they flagged it as Spyware.
[+] Answer : Spyware.HawkEyeKeyLogger
[+]
This question asks about the web server software , To get your answer you have to check the response HTTP packet came form the server because it has information about the server including web server software name , When you filter the content with HTTP protocol you will get two packets about the malicious server that malware came from
[+] Answer : LiteSpeed [+]
This question indicates that the user connected to any external website that offer information about his public IP.
After checking HTTP requests/responses, I got this domain "bot.whatismyipaddress.com" , check the response packet of this request.
[+] Answer : 173.66.146.112 [+]
Here we are talking about E-mail server , So we have to filter with SMTP(simple mail transfer protocol) protocol , The location of the mail server it will depend on the IP address as a previous questions we got locations via IP address from websites like ipinfo.io but in this question will find the location using wireshark.
[+] Answer : United States [+]
Meaning of this question is the domain of the sender e-mail , So we have to check the SMTP packets content , To see all packets contents of SMTP.
Right click on any SMTP packet → Follow → TCP Stream.
Put this domain in any whois website like this
[+] Answer : 2014-02-08 [+]
From the first response packet from SMTP server the banner of the software says it's Exim version 4.91
[+] Answer : Exim 4.91 [+]
The E-mail is sent to himself , It sounds like it's a stealer software :D
[+] Answer : sales.del@macwinlogistics.in [+]
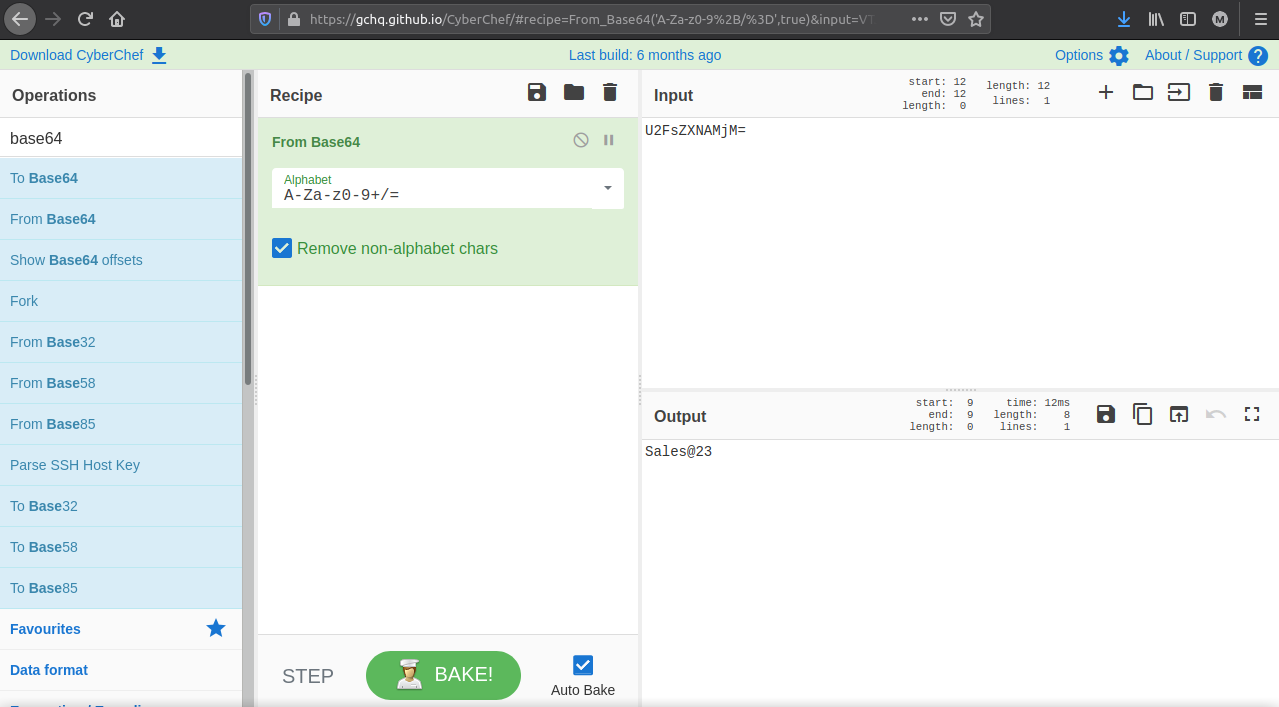
From the TCP stream of the SMTP packets we see AUTH process and the arguments of this auth encoded with base64 to decod this data you can use linux or website like cyberchef
[+] Answer : Sales@23 [+]
To discover these informations you have to decode the base64 message content
After decoding the data it will show up
[+] Answer : Reborn v9 [+]
From the encoded date send , After decode the data it will show information about login credentials for bankofamerica.
[+] Answer : roman.mcguire:P@ssw0rd$ [+]
From SMTP packets , it appears it's sending the DATA every 10 mintues , You can calc by sub the seconds value between every Data packets sent and divided it with 60 , 60 is number of seconds in mintue.
[+] Answer : 10 [+]























































Post a Comment